A Roadmap to Going Passwordless

For years, “going passwordless” was little more than a pipe dream. Although it was clear to both security professionals and consumers that passwords were ineffective and full of friction, most companies felt powerless to phase them out because there simply was no tenable alternative. Fortunately, that’s no longer the case. Thanks to major advances in technology and new regulations on the horizon, the move toward passwordless technology has reached a critical tipping point. Every day, new companies are phasing out passwords and replacing them with a higher security and more frictionless solution: the mobile phone. In a recent webinar, Bill Fish, VP of Authentication of Prove, and Cameron D’Ambrosi, Senior Principal at Liminal, review the simple steps every company should take to go passwordless.
What’s wrong with passwords?
BF: First off, passwords are not secure because they are reused frequently by the consumer across websites. They’re also inefficient because customers forget them frequently. As a result, many consumers resort to contacting the call center for log-in support, driving up costs. Because of all this friction, passwords lead to negative perceptions. By going passwordless, companies can save money by reducing customer support costs while preventing more fraud and improving user experience.
CD: For the longest time, there was a notion that authentication and cybersecurity practices live in a part of the company that is totally separate from the growth team. This is a critical mistake because customers don’t think of it like this. Your brand is inexorably linked to how the customer is authenticating themselves. Smart digital authentication is now a competitive advantage.

If passwords don’t work, what does?
BF: There are three forms of authentication: something you know, something you have, and something you are (aka inherence). Traditionally, the “something you know” requirement has been fulfilled by the password; an OTP sent via SMS fulfills the “something you have category”; and face scans and other biometrics fulfill the “something you are” category. In order to leverage multi-factor authentication, your flow must include at least 2 of those 3 major categories.
Today, the mobile phone is replacing the password because it fulfills multiple means of authentication. For example, an SMS OTP could be sent to the phone (fulfilling the “something you have” requirement) and a face scan could be used on the phone to fulfill the “something you are” requirement.
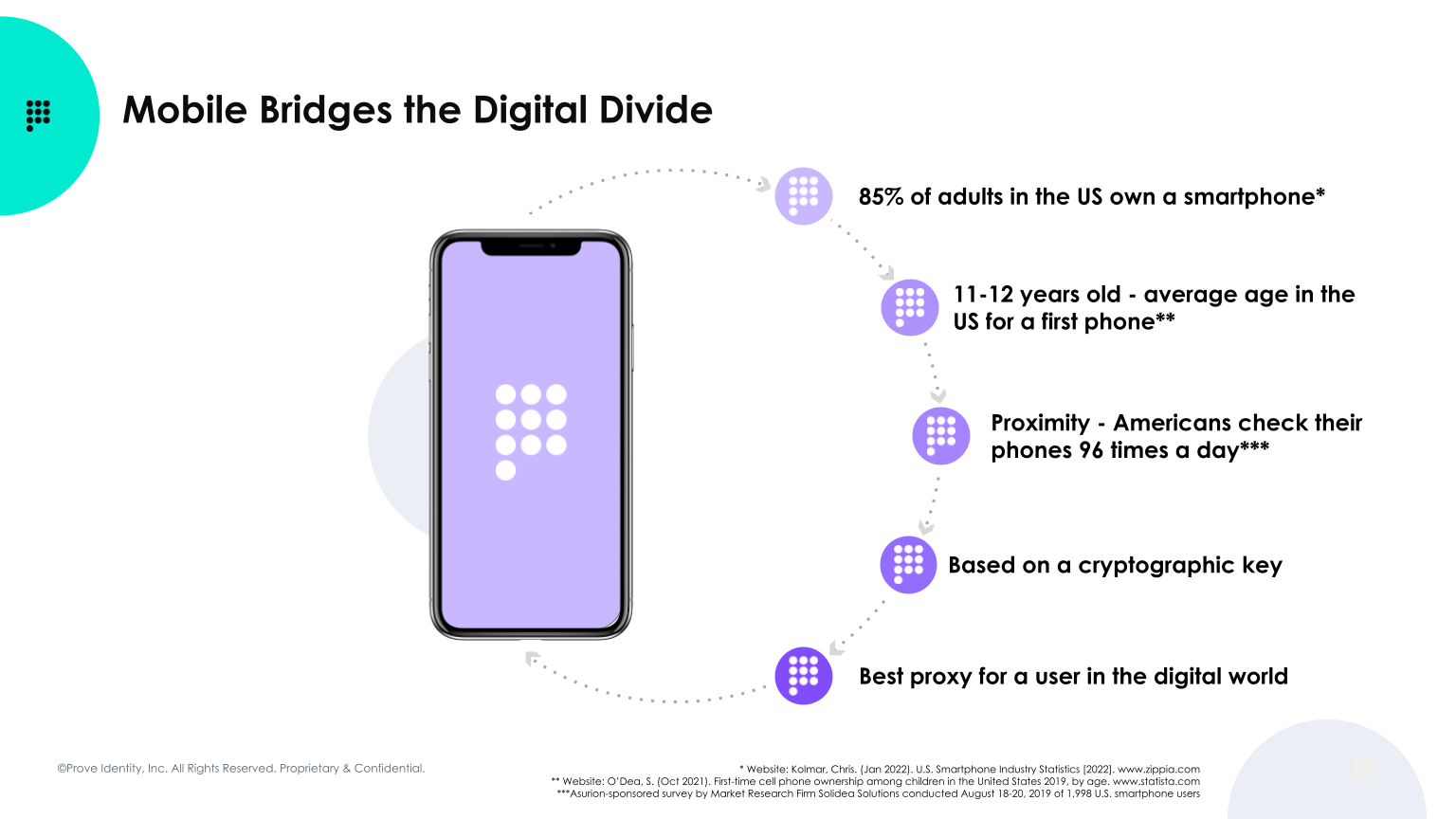
The phone’s ubiquity in modern life also contributes to its usefulness as a replacement for passwords. Today, the mobile phone really is the bridge between the physical and digital worlds. Kids get phones when they are about 11 years old and the vast majority of adults in the US own a smartphone. For most people, phones are practically always within arm’s reach. In fact, they’re checked about 96 times a day.
CD: A major benefit of the mobile phone is you can leverage the cryptographic key (SIM Card) that talks to the mobile network. Most people don’t realize how sophisticated the encrypted technology of the SIM card really is. The SIM card remains super secure. Because of the ubiquity of the mobile phone and the level of security inherent in the SIM card, very few options are better.
How does passwordless technology work?
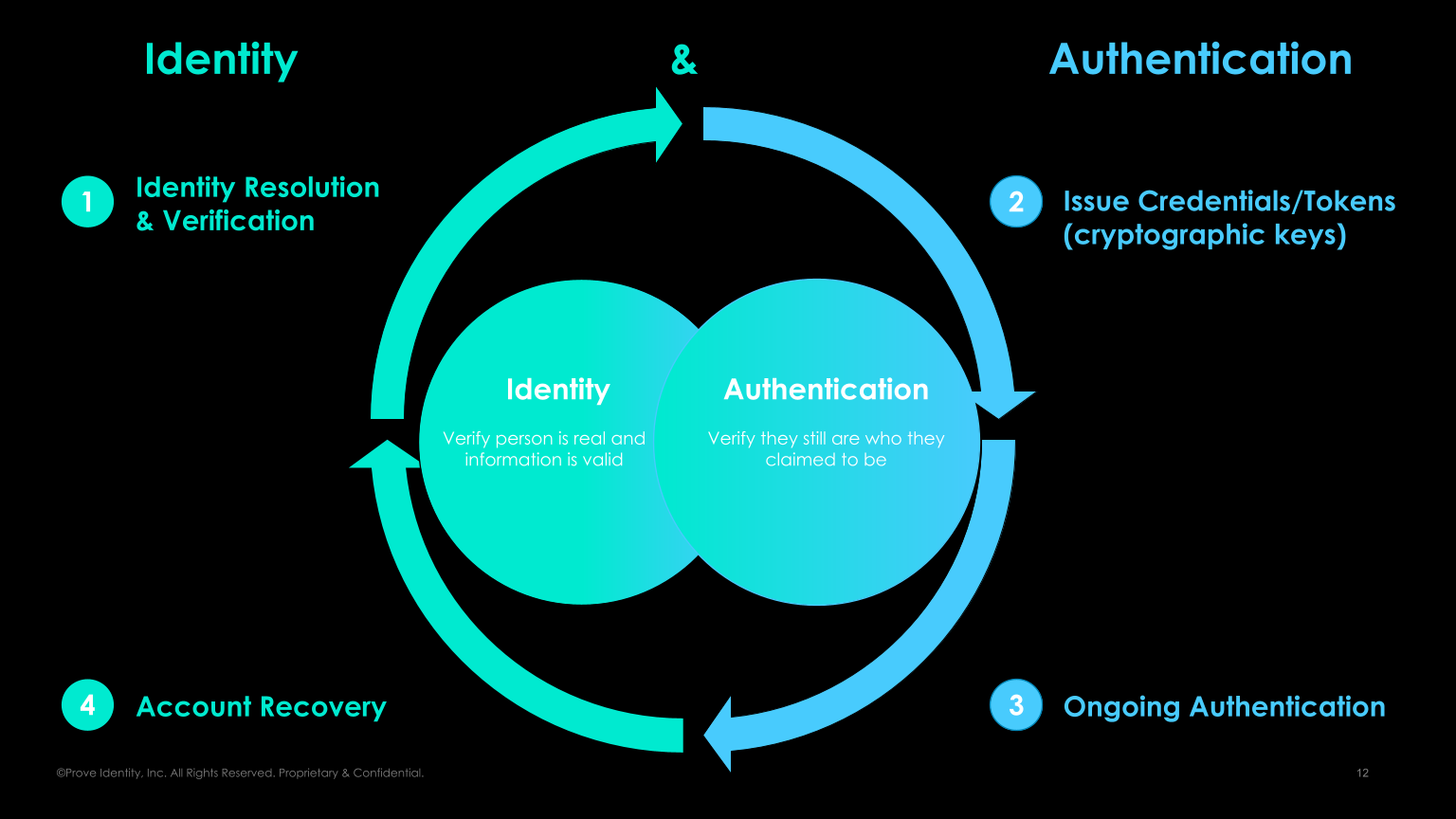
BF: When the user is first showing up, you want to establish the passwordless credentials as quickly as possible. You then have your ongoing authentication that no longer requires passwords. But what happens when you buy a new phone? You need an efficient account recovery process.
What is a good road map for going passwordless?
BF: There have been a lot of companies pushing for passwordless for years and years. We are finally approaching a tipping point where we can get that rock over the hill.
If you do not currently have a form of second-factor authentication, the very first step you need to do is to get one ASAP. This is an important first step because it improves security and you get a phone number that helps with contactability. Prove does this really well because our methodology makes this super easy. We get customers onboarded faster and reduce fraud.
Another important step is to assess how you want to interact with users. A company that operates solely with a mobile app will have very different requirements than a company that leverages call centers or a user’s desktop, for instance. If your company has multiple secondary channels, it’s important to find ways your consumers can leverage the phone for authentication and verification purposes in every channel. One of the popular ways to do this is with a QR code or a link sent via SMS.
Finally, another really important step is to consider what happens when a user purchases a new phone or there is a break-the-glass account recovery scenario. How do you verify your identity on a new phone? What happens if the device is jailbroken? If you have a strong foundation of an identity-proofing event, you can use that same methodology to rebind.

Want a custom roadmap to going passwordless? Speak with a digital identity expert today.

Keep reading
 Read the article: The Death of the OTP: Why Legacy MFA is Failing the Modern Consumer
Read the article: The Death of the OTP: Why Legacy MFA is Failing the Modern ConsumerDiscover why legacy MFA is failing and how Prove Unified Authentication provides a smarter, frictionless alternative. Learn how to replace insecure SMS OTPs with continuous, multi-layered identity assurance that prevents fraud while boosting conversion rates.
 Read the article: Prove Launches ProveX℠, the Internet’s First Digital Trust Exchange
Read the article: Prove Launches ProveX℠, the Internet’s First Digital Trust ExchangeProve launches ProveX, ProveX, a new digital trust exchange that enables enterprises to instantly access verified data and credentials from partners, while preserving trust through every interaction
 Read the article: Beyond the OTP: Why SMS-Based 2FA Is Failing and What Comes Next
Read the article: Beyond the OTP: Why SMS-Based 2FA Is Failing and What Comes NextExplore the classic conflict between security measures and user friction.













