Choosing the Right Authentication Protocol: A Developer's Guide to SAML and OpenID Connect

Authentication is the process of verifying the identity of an entity (user, device, or system) to ensure they are who they claim to be. It is important to make sure that only authenticated users can access your system. This applies whether you are creating a large application or a cloud service.
As a developer, you need authentication to safeguard your application and ensure that only legitimate users can interact with it. Authentication is also important for maintaining user trust and complying with regulatory standards. It usually involves one or more factors, such as something you know (passwords or PINs), something you have (security tokens or smart cards), and something you are (biometric data, like fingerprints or facial recognition).
If you’re looking to implement an authentication mechanism based on something you know, protocols like Security Assertion Markup Language (SAML) and OpenID Connect (OIDC) are a great choice. These protocols help you offload authentication management, reducing the risks and complexities of handling user credentials directly. These protocols can also be extended to support multifactor authentication (MFA).
In this guide, you’ll compare SAML and OIDC, looking specifically at how each protocol works and when to choose one over the other.
SAML vs. OIDC
SAML and OIDC are standards designed to provide secure authentication for users across applications. However, they’re built for different contexts and offer distinct advantages.
What Is SAML
SAML is an open standard that enables single sign-on (SSO) by allowing users to authenticate once and access multiple applications without needing to log in again. SAML facilitates communication between an identity provider (IdP, the entity verifying the user’s identity) and a service provider (the application the user wants to access).
How SAML Works
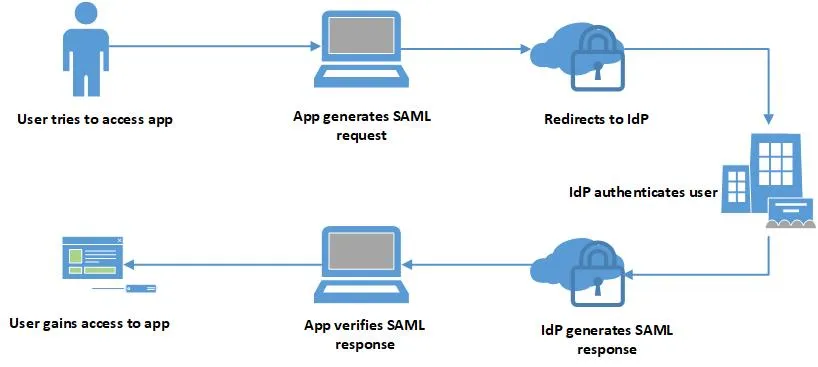
Imagine you’re developing a project management app that your company’s employees will use. Instead of building a custom login system, you decide to integrate SAML. A simple SAML workflow looks like this:
- An employee attempts to access your project management app.
- Instead of handling the login yourself, your app redirects the user to the company’s IdP; for example, Okta and Microsoft Entra ID.
- The IdP prompts the user to log in (if they haven’t already) and verifies their credentials.
- Once authenticated, the IdP sends a signed XML document, called a SAML assertion, back to your app. This assertion contains details like the user’s identity and permissions.
- Your app validates the assertion, confirms the user’s identity, and grants access.
This setup simplifies user management for you because authentication is centralized with the IdP. If your organization uses multiple apps, employees need only one set of credentials to access the apps, but a more complex SAML workflow may apply.
Pros of SAML
- SSO: SAML simplifies the user experience by allowing users to authenticate once and access multiple applications without logging in again. This reduces password fatigue and enhances productivity, particularly in enterprise environments with numerous applications.
- Legacy system compatibility: SAML works well with older systems that use XML-based protocols. This makes it an attractive option for businesses wanting to connect easily with their existing infrastructure.
- Strong security: SAML offers robust security features, such as XML-based assertions, digital signatures, and encryption. These mechanisms ensure that identity information is securely transmitted and tamper-proof.
- Standardized and mature: SAML is a well-established standard with widespread adoption. The SAML authentication market is expected to be worth $3 billion USD by the end of 2024. Its maturity means it is thoroughly vetted, widely supported, and backed by a strong ecosystem of tools and documentation.
Cons of SAML
- Complexity of XML processing: Since SAML relies heavily on XML, it can be challenging to handle, especially in mobile apps, because the assertions are huge payloads.
- Vulnerabilities from incorrect XML processing: Improper handling or parsing of XML can introduce vulnerabilities, such as injection attacks or data manipulation, which can compromise security.
When to Choose SAML
SAML excels in traditional enterprise environments. Following are some key use cases:
- Federation and cross-domain authentication: Choose SAML for federated identity scenarios, where users need to authenticate across multiple domains or organizations. SAML is commonly used in B2B scenarios where one organization needs to trust the IdP of another for seamless authentication.
- SSO across multiple applications: SAML can be used across enterprise applications that require SSO access across web-based applications, intranet systems, and more.
- Legacy systems compatibility: SAML works well with older systems like a legacy core banking system or a hospital’s legacy electronic health record (EHR) system that is built on XML-based protocols and can’t handle modern authentication mechanisms like OAuth or OpenID Connect.
- More complex user attributes: SAML allows for complex user attribute mapping and detailed information exchange in the form of SAML assertions. If your application requires a high level of detail regarding the user’s attributes, such as roles, groups, and entitlements, SAML may provide more flexibility.
What Is OIDC
OIDC is a modern authentication protocol built on top of OAuth 2.0. It allows applications (known as relying parties) to verify a user’s identity. They can also get basic profile information through standardized ID tokens, which are encoded in a JSON Web Token (JWT) format. OIDC is particularly suited for API-driven, mobile, and modern web applications because it supports flexible, lightweight, and secure authentication flows.
OIDC uses scopes to define what level of access and what specific information an application can request from the user’s identity. Scopes are like permissions that the user agrees to when logging in. For example, the OpenID scope is mandatory and allows the app to perform authentication and retrieve basic identity details.
Additional scopes like profile, email, or address grant access to specific user information, such as their name, email address, or physical address. The IdP uses these scopes to tailor the tokens (like the ID token) or API responses.
How OIDC Works
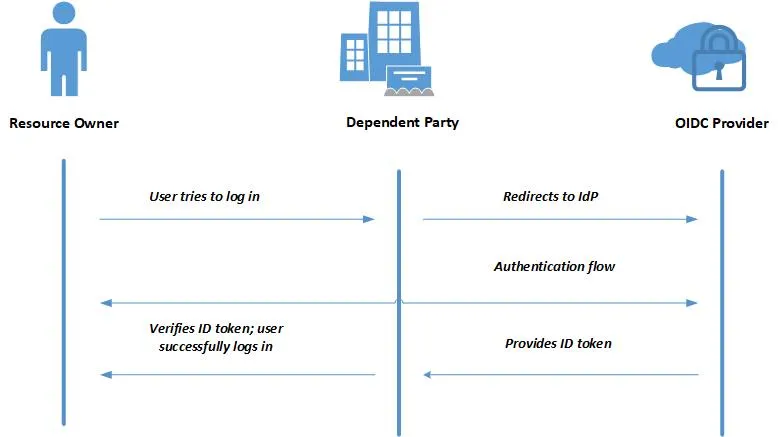
Imagine you’re developing a mobile app that allows users to access a personalized dashboard. Instead of building your own login system, you implement OIDC with a third-party IdP like Google. In a simplified client-side-only architecture, this is what the process would look like:
- You sign up on the IdP’s developer portal and register your mobile app by providing details like your application name and your redirect URL.
- The IdP (Google) generates a client ID for your app.
- You access the IdP’s discovery document URL to retrieve key metadata, like the authorization endpoint, UserInfo endpoint, public keys, and supported scopes.
- When the user selects Sign in with Google, your mobile app redirects them to Google’s authorization endpoint (login page) to authenticate users and obtain their consent for data sharing with parameters such as response_type, client_id, and scopes.
- Google (the IdP) prompts the user to log in using their Google credentials. The user then grants consent for your app to access requested scopes like profile info and email.
- After successful authentication, Google generates an ID token (JWT) containing the user’s identity and redirects the user back to your redirect URL with the id_token and access_token.
- Your app validates the tokens and then grants the user access. It uses the info from the ID token and UserInfo endpoint to personalize the user’s dashboard.
Note that this is just one of the flows supported by OIDC. There are several others as well.
Pros of OIDC
- Optimized for modern applications: OIDC is designed with modern web and mobile applications in mind. It uses JWT, which is compact, easy to parse, and well-suited for handling authentication in mobile and web apps.
- SSO-enabled: OIDC enables SSO across multiple applications, allowing users to authenticate once and access various services.
- Built on OAuth 2.0: OIDC extends OAuth 2.0, a well-established authorization framework. This means OIDC can handle both authentication and authorization in a single protocol, which is efficient for modern app architectures.
- Mobile and API-friendly: OIDC supports mobile apps and APIs. Its lightweight nature and focus on JSON-based communication make OIDC a perfect fit for mobile-first and API-driven architectures.
- Federated identity management: OIDC allows users to authenticate through third-party IdPs, such as Google and Facebook, which reduces the need to manage multiple credentials.
Cons of OIDC
- Relies on third-party providers: Since OIDC often relies on third-party IdPs, if the IdP experiences downtime or a breach, it can affect the availability or security of your application.
- Security risks with token handling: OIDC relies on JWTs for transmitting user identity information. Improper handling of tokens, such as storing them insecurely or not validating them properly, can introduce security vulnerabilities.
- Less support for legacy systems: OIDC is not always compatible with older, legacy systems that rely on protocols like SAML or older forms of authentication.
When to Choose OIDC
OIDC is the go-to protocol for modern, dynamic applications. Consider it for the following scenarios:
- Mobile applications: OIDC is optimized for mobile apps. Its lightweight, JSON-based tokens are easy to parse and work seamlessly with REST APIs commonly used in mobile app backends.
- API-driven and microservice architectures: OIDC is designed to handle token-based, stateless authentication and integrates naturally with APIs and microservices. Its ID tokens, encoded as JWTs, can be easily validated by different services without contacting the IdP repeatedly.
- Modern web applications: OIDC is a go-to choice for modern web apps. It’s designed to handle modern authentication needs from SSO across devices to federated identity and MFA.
- Cross-platform and cloud-native environments: OIDC excels in environments where applications span multiple platforms (web, mobile, IoT) or are hosted in the cloud. The protocol supports modern cloud-native systems, like Salesforce, Spotify, or Slack, and uses widely adopted standards, like JSON and HTTP.
- Federated identity and SSO: Unlike SAML, OIDC enables federated identity and SSO that work effectively for both web and mobile apps. This flexibility is particularly valuable for modern applications like Pinterest that integrate Google and Facebook for federated identity, allowing users to log in with their existing credentials.
- Scalability and future-proofing: OIDC adapts to the evolving needs of modern applications. Its design and modern architecture align with current and emerging authentication requirements like social login, token-based authentication, and fine-grained access control to manage permissions for different resources. It also supports advanced features like dynamic client registration and OpenID extensions for future enhancements.
Conclusion
In this article, you learned that SAML is ideal for enterprise environments with legacy systems. It offers robust security and SSO for large-scale applications. In contrast, OIDC is optimized for modern, mobile-first, and API-driven applications, providing a lightweight authentication solution that integrates well with cloud-native environments. Choosing the right protocol depends on your application’s specific needs, such as legacy system compatibility, mobile or API requirements, and scalability.
As you decide which authentication method is the right one for your project, it’s important to consider factors like security, user experience, and the complexity of onboarding and identity verification. Prove is a modern solution for identity verification and authentication.
It dynamically verifies key personal information and assesses risk. This enables businesses to streamline user onboarding and build trust over time. From account creation to ongoing verification, Prove simplifies identity management for a seamless and secure experience.

Keep reading
 Read the article: Prove Launches Global Identity Graph to Redefine Digital Trust for 90% of Digital Consumers
Read the article: Prove Launches Global Identity Graph to Redefine Digital Trust for 90% of Digital ConsumersProve has launched its Global Identity Graph, a foundational platform that connects verified human identities to their digital tokens, redefining digital trust and enabling instant, frictionless, and secure engagement for over 90% of digital consumers worldwide.
 Read the article: Prove Partners with Hard Rock Bet to Deliver Elite Onboarding and Enhance Player Experience
Read the article: Prove Partners with Hard Rock Bet to Deliver Elite Onboarding and Enhance Player ExperienceProve and Hard Rock Bet partner to deliver elite player onboarding by using Prove Pre-Fill® to instantly verify identities, streamline signup, and enhance security in online gaming.
 Read the article: Prove and Backbase Partner to Enable Faster and Safer Onboarding for Financial Institutions
Read the article: Prove and Backbase Partner to Enable Faster and Safer Onboarding for Financial InstitutionsThe Prove Pre-Fill solution integrates with Backbase’s AI-powered Banking Platform to reduce fraud, streamline data entry, and improve digital account opening experiences.













