How to Streamline Identity Verification with Minimal User Friction Using KYC Software

Know Your Customer (KYC) software automates the mandatory process of verifying a customer's identity when they open an account and, occasionally, over time. It's how regulated industries prevent fraud and ensure regulatory compliance.
However, automation alone isn't enough—it must also meet regulatory requirements. According to Forrester's 2023 True Cost of Financial Crime Compliance study, 82 percent of financial institutions must adhere to strict regulations, while 85 percent also prioritize improving user experience.
Striking the right balance between compliance and a seamless user experience is challenging. However, incorporating KYC doesn't have to mean sacrificing user experience. With the right tools, you can effectively balance both compliance and user experience. This article explores some of the features that KYC tools offer as well as best practices for reducing user friction.
Traditional Identity Verification Issues
Despite the availability of automated identity verification tools, many organizations still rely on manual processes. According to Fenergo, a leading KYC and onboarding solutions provider, many financial institutions heavily depend on manual steps, which increases onboarding costs. Consequently, new customers often have to submit physical documents and wait for back-office reviews, which is not only annoying but also time-consuming.
Back-office systems operate in silos, forcing compliance officers to manually cross-check data across multiple databases. Without automated tools, teams must manually extract and enter information from various documents, increasing the chance of errors.
This challenge grows even more complex with international customers, who bring not only different document types and compliance formats but also diverse privacy regulations. For example, some areas have strict data localization laws. They also require clear consent under rules like the General Data Protection Regulation (GDPR). This adds yet another layer of complexity to the verification process.
Forrester's study also highlights escalating compliance costs, with 98 percent of institutions reporting increases in both direct costs (like manual processing) and indirect costs (like delayed onboarding).
Understanding KYC Software
Modern KYC software provides a suite of verification tools across multiple data sources. These software solutions continuously monitor customer profiles and transactions. They also aggregate data to generate risk scores, helping organizations maintain compliance throughout the customer lifecycle.
Different industries use KYC software for varying reasons. Banks and financial institutions use it for customer due diligence (CDD) and enhanced due diligence (EDD) during account opening and monitoring. Cryptocurrency platforms use it to comply with anti-money laundering (AML) regulations while keeping onboarding fast. Insurance providers verify policyholder identities and assess risk, while fintech companies ensure compliance across regulations without compromising user experience:
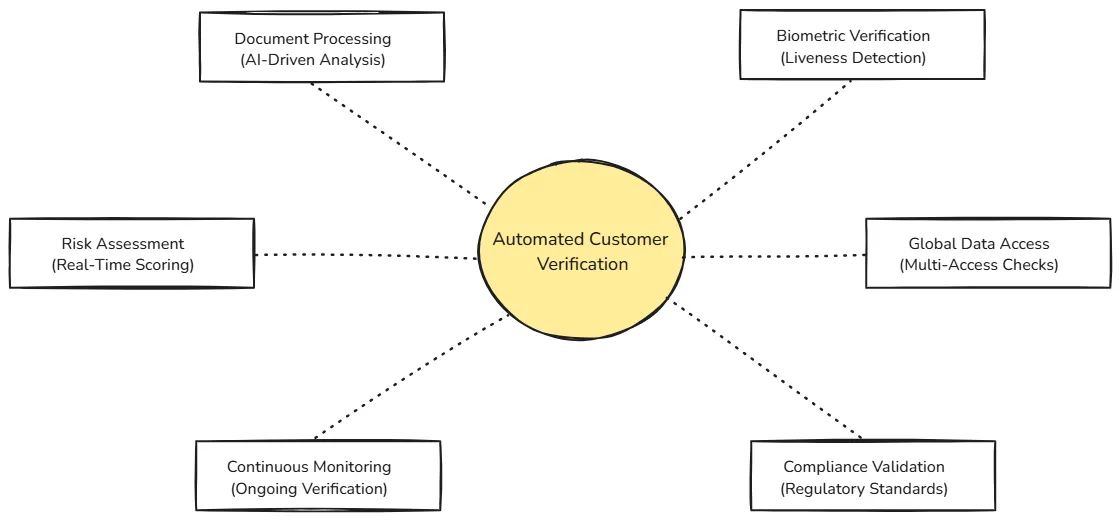
Each of these components—from AI document processing to continuous monitoring—feeds into a core verification process that aims to balance security, compliance, and speed.
Features of an Effective KYC Software
Effective KYC software integrates artificial intelligence (AI) and biometric capabilities to automate risk assessments, lower manual workload, and improve reliability.
Automation and AI Integration
AI engines for document analysis (computer vision), text extraction (natural language processing (NLP)), and signature verification (pattern recognition) analyze and verify submitted documents in real time. For instance, KYC software might use optical character recognition (OCR) to scan a driver's license, extract the owner's name and date of birth, and check for authenticity markers. Convolutional neural networks (CNN) perform image analysis, quickly flagging suspicious documents and generating real-time risk scores.
Biometric Verification
Biometric verification adds another security layer by confirming a user is physically present and matches their ID. Common methods include facial recognition with liveness detection, fingerprint scanning, and voice recognition.
However, real-world data breaches like Signzy, Transak, and Fractal ID, highlight the privacy risks of storing biometric data in centralized repositories.
To mitigate these threats, some providers adopt on-device processing, as seen with EnQualify, which uses AI at the mobile edge to keep sensitive information on the user's device.
Global Data Access and Compliance
Modern KYC platforms cross-reference multiple data sources, including government records and international sanctions lists, to verify user identities in real time. Common watchlists include the US Office of Foreign Assets Control (OFAC) list, politically exposed persons (PEP) lists, and consolidated sanctions lists from entities like the United Nations and the European Union.
Many jurisdictions impose their own regulatory requirements—such as the Financial Action Task Force (FATF) recommendations or the EU Anti-Money Laundering Directives (AMLD). To stay compliant, KYC software integrates with APIs that continuously update watchlists. The Prove Identity solution streamlines this process by verifying individuals against global sanctions and PEP databases, including OFAC, the EU Financial Sanctions List, and the UN Sanctions List. This ensures organizations maintain robust AML/KYC compliance across multiple regions.
User-Friendly Interfaces
Designing KYC software with an intuitive interface significantly reduces user friction through clear instructions, minimal clutter, dynamic tooltips, and automated data validation. Confusing workflows and errors drive up support inquiries and onboarding drop-offs, so it's critical to provide immediate in-app feedback, simple form layouts, and localized language support. According to DashDevs, a well-designed UX increases conversion rates by up to 400 percent.
Strategies to Minimize User Friction with KYC Software
User friction can delay payments and cause frustration. Here are four strategies to minimize friction when implementing KYC software.
Tiered Verification Approaches
Tiered verification is a risk-based approach that allows new customers to access basic services with minimal verification and then gradually increases security requirements as the user attempts higher-risk services. The FATF outlines factors to consider when determining risk levels and categorizing users into different tiers.
Real-Time Feedback
Effective verification systems need to be able to inform users immediately when there's a problem with their submitted documents, such as blurry images or missing information. For example, when a user takes a photo of their ID, the system should check if all corners are visible, the text is readable, and there's no glare—before the user submits it.
With real-time feedback, it's important to ensure that error messages are specific and actionable—telling users exactly what's wrong and how to fix it. Generic messages like "verification failed" or "invalid document" create confusion and increase support requests. Instead, messages should guide users with clear instructions like "The text on your ID is blurry. Please retake the photo in a well-lit area and make sure all text is clear." This kind of detailed feedback helps users correct issues quickly and complete verification successfully with as little frustration as possible.
Mobile-First Design
Mobile verification has to go beyond making desktop screens smaller. Apps have to use smartphone features that users already have—like cameras and fingerprint sensors—to make verification easier. When users try to capture their ID, the app should help position the camera correctly, check lighting conditions, and confirm image quality immediately. Phone signals like SIM card data and phone number verification should be used to confirm someone's identity without asking for extra documents.
The app must also work well even when users have poor internet connection or older phones. This means keeping file sizes small without losing important document details and saving partially completed forms so users don't lose their progress.
Prove uses a phone's built-in signals to verify identity, streamlining the process for users without compromising security.
Transparency and Trust Building
Establishing trust begins with clearly explaining why user data is collected and how it will be used. Customers feel more comfortable sharing sensitive information when they understand its purpose and know that their data won't be misused.
Privacy policies should clearly state data retention periods, encryption methods, and user rights regarding data access or deletion. Visual cues—like lock icons, color-coded fields, tooltips, or explanatory links—reinforce transparency.
Selecting the Right KYC Software
When assessing KYC tools, make sure you consider these three critical factors: scalability, integration capabilities, and multi-jurisdictional compliance coverage.
Scalability
Scalability in a KYC solution means handling high volumes of concurrent verification requests without degrading performance. Your software should distribute processing loads across multiple servers, cache verification results to avoid redundant checks, and store user verification data efficiently for quick retrieval. This is especially crucial during peak registration windows, such as product launches or large marketing campaigns, to maintain a seamless user experience.
Look for solutions that are cloud-based with distributed architecture. This means the system can automatically add more computing resources during high-traffic periods and scale back during quieter times. Moreover, pay attention to the provider's uptime guarantees and response time metrics—these indicate how well the system performs under load.
Integration Capabilities
Product teams often have problems with KYC software. This software may need duplicate data entry. It can also create inconsistencies between systems. For example, customer data in the KYC system might not match the user management database.
Your KYC solution must provide clear integration options through well-documented APIs, SDKs for both web and mobile platforms, and webhook support for real-time notifications. This way, when a user starts verification, the KYC software automatically pulls existing user data, updates the verification status, and maintains consistent records across all systems.
Prove provides comprehensive implementation guides, developer resources, blogs, and extensive API references, making it easier to integrate KYC processes into existing systems.
Make sure your KYC provider's integration time matches your project timeline. Simple API integrations might take days, but complex custom requirements could extend the timeline. Before choosing your solution, also make sure it supports your tech stack and can connect to your critical systems like user databases, compliance reporting tools, and transaction monitoring platforms.
Multi-jurisdictional Compliance Support
In the US, customers commonly verify their identity with social security numbers (SSN) and driver's licenses. EU customers need explicit consent for data processing and have the right to request data deletion under GDPR. Meanwhile, Singapore requires National Registration Identity Card (NRIC) verification and local data storage.
Your KYC solution needs to handle multiple regulatory requirements—including PEP, AML, Customer Identification Program (CIP), and Telephone Consumer Protection Act (TCPA) compliance. Look for KYC providers that regularly update their compliance rules and document how they handle regional differences. The software should automatically detect which requirements apply based on user location and adjust document requests accordingly.
For instance, if your app expands to a new region, the verification flow should automatically update to accept local ID types and follow local privacy laws without requiring major changes to your integration.
Some Modern KYC Approaches
So far, the discussion has been on strategies that ensure a reliable KYC process with minimal user friction. A modern KYC tool must be able to integrate these best practices and can strengthen your identity verification setup.
Building a reliable and secure KYC system often requires integrating multiple verification channels, each leveraging different APIs. One such channel is the Prove Trust Score, a phone-centric solution that evaluates phone number activity to detect risks like SIM swaps, disposable numbers, or mismatched carrier information. Combining the document verification of Jumio with the phone intelligence of Prove enables businesses to establish a multi-layered KYC process that reduces the risk of identity theft and synthetic identities.
Incorporating solutions like the Prove Identity Manager℠ enhances the verification process with a phone-centric data approach to user identity. This extra layer of security validates phone numbers through device and network intelligence, performing real-time checks on ownership and activity patterns.
Conclusion
Implementing effective KYC software requires balancing security, compliance, and user experience. This article explored how modern solutions automate traditional manual processes through AI-powered document processing, biometric verification, and real-time database checks. Tiered verification approaches, real-time feedback, mobile-first design, and clear error handling can help reduce user friction while maintaining security standards.
As organizations improve their verification systems, adding phone intelligence gives an extra layer of security without compromising user experience. To learn more about adding phone-based intelligence to your KYC platform, check out the Prove Developer Portal and see how their phone-centric approach can strengthen your existing infrastructure.

Keep reading
 Read the article: Prove Launches Global Identity Graph to Redefine Digital Trust for 90% of Digital Consumers
Read the article: Prove Launches Global Identity Graph to Redefine Digital Trust for 90% of Digital ConsumersProve has launched its Global Identity Graph, a foundational platform that connects verified human identities to their digital tokens, redefining digital trust and enabling instant, frictionless, and secure engagement for over 90% of digital consumers worldwide.
 Read the article: Prove Partners with Hard Rock Bet to Deliver Elite Onboarding and Enhance Player Experience
Read the article: Prove Partners with Hard Rock Bet to Deliver Elite Onboarding and Enhance Player ExperienceProve and Hard Rock Bet partner to deliver elite player onboarding by using Prove Pre-Fill® to instantly verify identities, streamline signup, and enhance security in online gaming.
 Read the article: Prove and Backbase Partner to Enable Faster and Safer Onboarding for Financial Institutions
Read the article: Prove and Backbase Partner to Enable Faster and Safer Onboarding for Financial InstitutionsThe Prove Pre-Fill solution integrates with Backbase’s AI-powered Banking Platform to reduce fraud, streamline data entry, and improve digital account opening experiences.













