Top 5 API Best Practices for Identity Verification Solutions


With cyber threats escalating and data privacy regulations tightening worldwide, identity verification APIs have become the anchor of secure, compliant digital interactions. Implementing these APIs is not just about adding code, however. Careful integration of identity verification capabilities across various tools and applications is critical to unlock their full potential.
In this blog, we'll explore the top five best practices for integrating identity verification APIs. Included are insights into optimizing performance, securing data, and creating a seamless user experience. After finishing, you will have the knowledge needed to deploy robust, compliant, and user-friendly identity verification solutions.
Best Practice #1: Prioritize Security at Every Integration Step
Handling sensitive user data demands strict security measures to protect against breaches and unauthorized access. You should protect every step of your integration to ensure that personal information remains confidential and tamper-proof.

Key Tips
- Use HTTPS for Data Encryption: Always use HTTPS to encrypt data when sending. This ensures that others cannot intercept or change the information between your application and the identity verification API.
- Implement Strong Authentication Protocols: Secure API access by implementing robust authentication methods, such as OAuth. This protocol validates that only authorized entities can interact with the API.
- Secure API Key Storage: API keys are the lifeline to accessing services — treat them as such. Avoid hardcoding API keys in your application or storing them insecurely. Instead, use secure storage methods like environment variables or dedicated secret management tools to prevent unauthorized access.
Prove’s Security Features
Prove’s identity verification APIs are equipped with advanced security features designed to protect data and ensure compliance. Prove utilizes tokenization to minimize the exposure of sensitive data, replacing actual data values with unique tokens that are meaningless if intercepted.
This ensures that we process and store personal information safely. These security features provide a trusted foundation, helping developers confidently integrate identity verification solutions.
Best Practice #2: Optimize API Calls for Efficiency and Performance
Reducing latency and optimizing API usage not only improve application performance, but also enhance the overall user experience by providing quick, reliable responses. Efficiency is key for identity verification. Prolonged wait times or repeated calls can lead to frustration and even security concerns.
Key Tips
- Minimize API Calls: Each API call consumes bandwidth and processing time, so aim to bundle requests wherever possible. Instead of making separate calls for different user data, send one request to get all the information at once. This way, you can gather everything you need in one go. It saves time and effort.
- Set Timeouts and Retries: Network reliability can change. Setting the right timeouts and retry strategies helps handle issues smoothly. This approach prevents overwhelming the network or backend. This approach ensures users receive feedback without the frustration of long wait times.
Prove’s Performance Optimization
Prove’s APIs are engineered for high-demand environments, delivering low-latency responses and scalable performance. Prove’s systems handle multiple requests quickly. This helps developers stay efficient without losing speed or reliability. This performance-focused design makes Prove’s identity verification solutions ideal for applications where quick, seamless responses are crucial.
Best Practice #3: Implement Robust Error Handling and Logging Mechanisms
Errors are inevitable in any integration, but how you handle them can make a significant difference. Good error handling and logging are important for keeping a reliable and user-friendly experience.
They also help make troubleshooting quick and effective. By catching and responding to errors in a clear way, you can lower user frustration. This also helps make your identity verification processes more stable.
Key Tips
- Gracefully Handle Common Errors: Anticipate and manage frequent issues, such as invalid input or network disruptions, by providing informative, user-friendly messages. This helps users see what went wrong and how to fix it. This improves their experience and trust in the app.
- Log Errors with Context: When errors happen, it helps to log them with enough context. Include details like request information, timestamps, and error codes. These logs can help with audits. They assist developers in understanding the order of events that caused an issue.
- Use Retry Logic with Exponential Backoff: For temporary network or server problems, retry failed requests with exponential backoff. This method helps the application slowly try to reconnect. This approach prevents overwhelming the server with repeated requests and increases the likelihood of a successful response.
Prove’s Documentation on Error Codes
Prove’s API documentation helps users manage errors effectively. It includes clear error codes and best practices for handling responses. Each error code provides guidance on how to interpret and respond to it. This gives developers the tools to manage issues effectively and maintain seamless functionality.
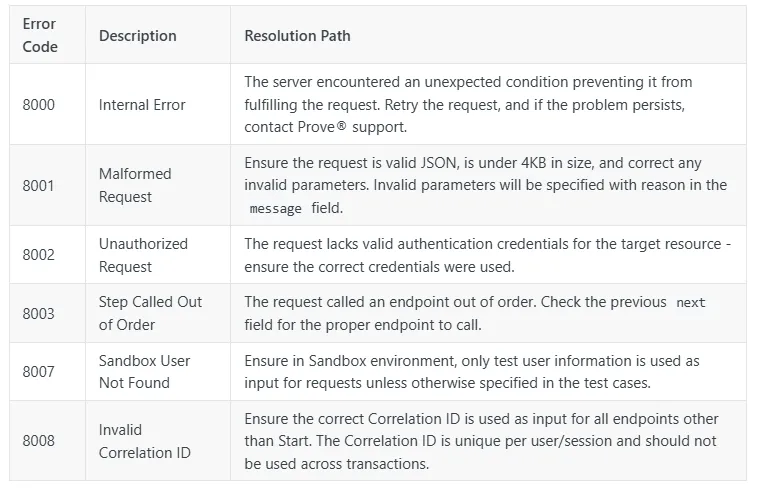
By following Prove’s recommendations, developers can troubleshoot and resolve issues efficiently, keeping their identity verification solutions reliable and user-friendly.
Best Practice #4: Ensure Compliance with Privacy and Data Protection Regulations
Following privacy laws when dealing with identity data is important. Two key laws are the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA). These rules are here to protect users' personal information.
Not following them can lead to serious legal issues and a loss of trust from users. A responsible approach to data handling is essential in every identity verification integration.
Key Tips
- Minimize Data Collection and Storage: Collect only the data that is absolutely necessary for identity verification, and avoid storing excessive or redundant information. This principle reduces the risk of data exposure and aligns with privacy regulations.
- Implement Secure Data Retention and Deletion Policies: Store data safely. Delete it when it is no longer needed. Secure deletion practices are essential for reducing data exposure over time.
- Conduct Regular Audits: Regularly auditing data handling practices helps maintain ongoing compliance as regulations evolve. Audits also identify areas for improvement in your processes, supporting a proactive approach to privacy.
Prove’s Compliance Support
Prove builds its tools with privacy and compliance as a core priority, helping developers meet regulatory standards seamlessly. Prove provides features like data tokenization and secure data storage to protect sensitive information and minimize exposure risks. Prove’s documentation and support provide guidance on best practices for data handling. This helps developers create solutions that follow industry rules and keep user data safe.
Best Practice #5: Use Developer Documentation and Support Resources Fully
API documentation is one of the most powerful tools available to developers. This roadmap significantly simplifies the integration process. By taking full advantage of the provided documentation, you can:
- Avoid common pitfalls
- Understand the API’s capabilities
- Deliver a more efficient and reliable implementation
Key Tips
- Review Prove’s API documentation carefully. Before you start the integration, take time to understand each feature, capability, and limitation. This upfront investment can help you plan a smooth integration and make the most of Prove’s functionality.
- Leverage Example Code and Implementation Guides: Prove’s documentation includes example code snippets and step-by-step implementation guides. Using these resources can help you work faster, learn best practices, and spend less time troubleshooting.
- Seek Additional Support When Needed: Prove’s support team provides valuable assistance, allowing you to connect with experts.
Prove’s Developer Portal
Prove’s Developer Portal is packed with resources to support every stage of the integration journey. By tapping into these resources, developers can tackle identity verification projects with greater confidence, efficiency, and success.
Conclusion
To integrate identity verification APIs well, you need to focus on security, performance, reliability, and compliance.
Ready to take your integration to the next level? Explore Prove’s comprehensive API documentation and developer resources. Dive into Prove’s tools and resources today to unlock the full potential of your identity verification solutions.
Photo by Théo Roland on Unsplash

Keep reading
 Read the article: Prove Launches Global Identity Graph to Redefine Digital Trust for 90% of Digital Consumers
Read the article: Prove Launches Global Identity Graph to Redefine Digital Trust for 90% of Digital ConsumersProve has launched its Global Identity Graph, a foundational platform that connects verified human identities to their digital tokens, redefining digital trust and enabling instant, frictionless, and secure engagement for over 90% of digital consumers worldwide.
 Read the article: Prove Partners with Hard Rock Bet to Deliver Elite Onboarding and Enhance Player Experience
Read the article: Prove Partners with Hard Rock Bet to Deliver Elite Onboarding and Enhance Player ExperienceProve and Hard Rock Bet partner to deliver elite player onboarding by using Prove Pre-Fill® to instantly verify identities, streamline signup, and enhance security in online gaming.
 Read the article: Prove and Backbase Partner to Enable Faster and Safer Onboarding for Financial Institutions
Read the article: Prove and Backbase Partner to Enable Faster and Safer Onboarding for Financial InstitutionsThe Prove Pre-Fill solution integrates with Backbase’s AI-powered Banking Platform to reduce fraud, streamline data entry, and improve digital account opening experiences.












